- About MAA
- Membership
- MAA Publications
- Periodicals
- Blogs
- MAA Book Series
- MAA Press (an imprint of the AMS)
- MAA Notes
- MAA Reviews
- Mathematical Communication
- Information for Libraries
- Author Resources
- Advertise with MAA
- Meetings
- Competitions
- Programs
- Communities
- MAA Sections
- SIGMAA
- MAA Connect
- Students
- MAA Awards
- Awards Booklets
- Writing Awards
- Teaching Awards
- Service Awards
- Research Awards
- Lecture Awards
- Putnam Competition Individual and Team Winners
- D. E. Shaw Group AMC 8 Awards & Certificates
- Maryam Mirzakhani AMC 10 A Awards & Certificates
- Two Sigma AMC 10 B Awards & Certificates
- Jane Street AMC 12 A Awards & Certificates
- Akamai AMC 12 B Awards & Certificates
- High School Teachers
- News
You are here
The Theorem that Won the War: Activities for Part 2.2 (Conjugates)
- Find \(P\), the permutation that shifts letters one place forward (so \(a \rightarrow b\), \(b \rightarrow c\), and so on). Also find \(P^{-1}\).
- Prove: \((P^{k}NP^{-k})^{-1} = P^{k}N^{-1}P^{-k}\).
- Consider the following initial setup for an Enigma encryption:
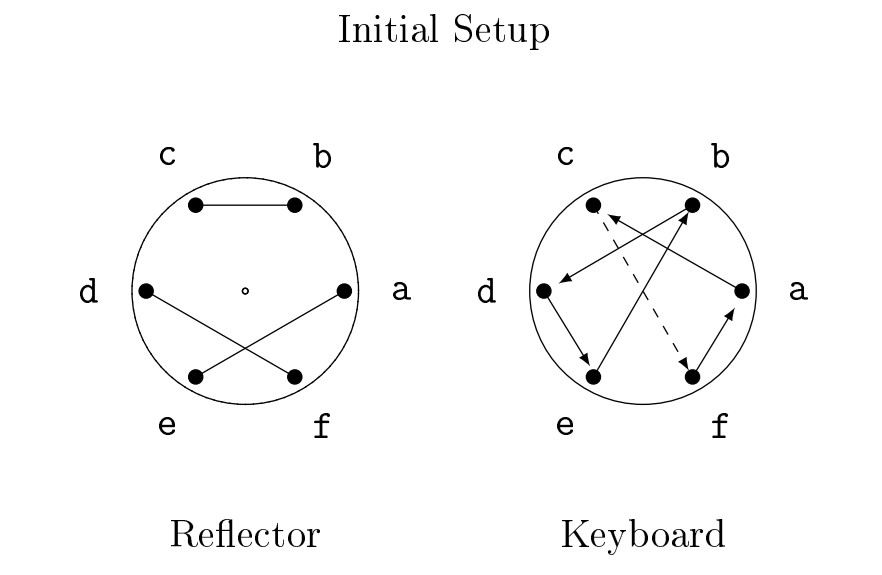
- Find \(Q\), the permutation corresponding to the reflector.
- Find \(N\), the permutation corresponding to the initial setup of the keyboard rotor. Also find \(N^{-1}\).
- Find the permutation \(P\) that shifts each letter one place forward (so \(a \rightarrow b\), \(b \rightarrow c\), and so on).
- Find the inverse permutation \(P^{-1}\).
- Compute \(PNP^{-1}\).
- Compute \(PN^{-1}P^{-1}\).
- Find \(E_{1}\), the permutation that will be used to encrypt the first letter.
- Verify \(E_{1} = PN^{-1}P^{-1} Q PNP^{-1}\). (Remember, in our paper Enigma we're ignoring the permutation \(S\) associated with the plugboard.)
- Find \(E_{2}\) and \(E_{3}\).
- The following explains the significance of the reflector. Using the reflector and keyboard setup shown above, answer the following.
- Consider an Enigma-type machine that omitted a rotor, so the \(k\)th letter of a message would use the permutation \(H_{k} = P^{k}NP^{-k}\). Find \(H_{1}\) and \(H_{1}^{-1}\).
- Show that by including the reflector \(Q\), the \(k\)th letter of an Enigma message would use the permutation \(E_{k} = H_{k}^{-1}QH_{k}\).
- Find \(E_{1}\) and \(E_{1}^{-1}\).
- Why does the reflector make the Enigma encryption easier to use?
Return to the overview of Part 2.2 (Conjugates).
Continue to the overview of Part 2.3 (Cycle Notation).
Jeff Suzuki (Brooklyn College), "The Theorem that Won the War: Activities for Part 2.2 (Conjugates)," Convergence (October 2023)




